About Us
CISO52 is a cybersecurity consultancy founded on the principle of fighting the "Triple Threat" in cybersecurity:(1) Data (2) Endpoint (3) IdentityBy executing security foundations exceptionally well, organizations can significantly enhance their security posture against the triple threat.
Perfect your security hygiene, and you eliminate the vast majority of risk. Execute the foundations well, and the rest will follow.Just as in life, where taking care of our mind and body leads to overall well-being, in cybersecurity, effective implementation of fundamental controls creates a strong foundation for comprehensive protection.
Our Philosophy
The Triple Threat
At CISO52, we recognize that attackers only need one weak point to compromise a system. That's why we champion on what we call the "Triple Threat"
Identity
Ensuring robust authentication and access control. An attacker only needs ONE open identity.
Endpoint
Securing all devices that connect to your network. An attack only needs ONE endpoint that is not protected.
Data
Protecting sensitive information at rest, in use, and in transit. An attacker only needs ONE sensitive file.
By addressing these three critical areas comprehensively, we help organizations build a resilient security infrastructure.
Our Approach
52 Security Ingredients
At CISO52, we've distilled the complex world of cybersecurity into 52 essential ingredients, mirroring the UNTOUCHABLE number in mathematics and the symbolic significance found in various aspects of life and culture.The U.S. Government Accountability Office (GAO) has designated 52 priority recommendations for addressing cybersecurity shortcomings in federal agencies. This alignment with our CISO52 framework underscores the critical nature of these elements in building a robust cybersecurity posture.The Australian Cyber Security Strategy 2023-2030 outlines multiple shields and actions to protect against cyber threats. Our 52 ingredients mirror this comprehensive approach, covering various aspects of cybersecurity from threat intelligence to incident response.In numerology, 52 is associated with introspection, analysis, and the expression of personal freedom. These qualities are essential in cybersecurity:
Introspection: Constantly evaluating and improving security measures
Analysis: Thoroughly examining threats and vulnerabilities
Freedom: Enabling secure digital operations without undue restrictions
Untouchable 52
The number 52 represents a complete cycle, much like the 52 weeks in a year. In cybersecurity, this symbolizes our commitment to providing year-round, continuous protection against evolving threats.Just as each week brings new challenges, our 52 essential ingredients ensure that organizations are prepared for the full spectrum of cyber risks they may face throughout the year
52 Weeks in a year
Continuous, year-round protection
52 cards in a deck
A complete set of cybersecurity solutions
52 white keys on a piano
Harmony in your security strategy
Power of 3
The 3 E's
Exposure:
Implementing controls across all systems
Effectiveness:
Optimizing configuration and support
Efficiency:
Breaking down complex challenges into actionable steps
Our Game
(Comin Soon)
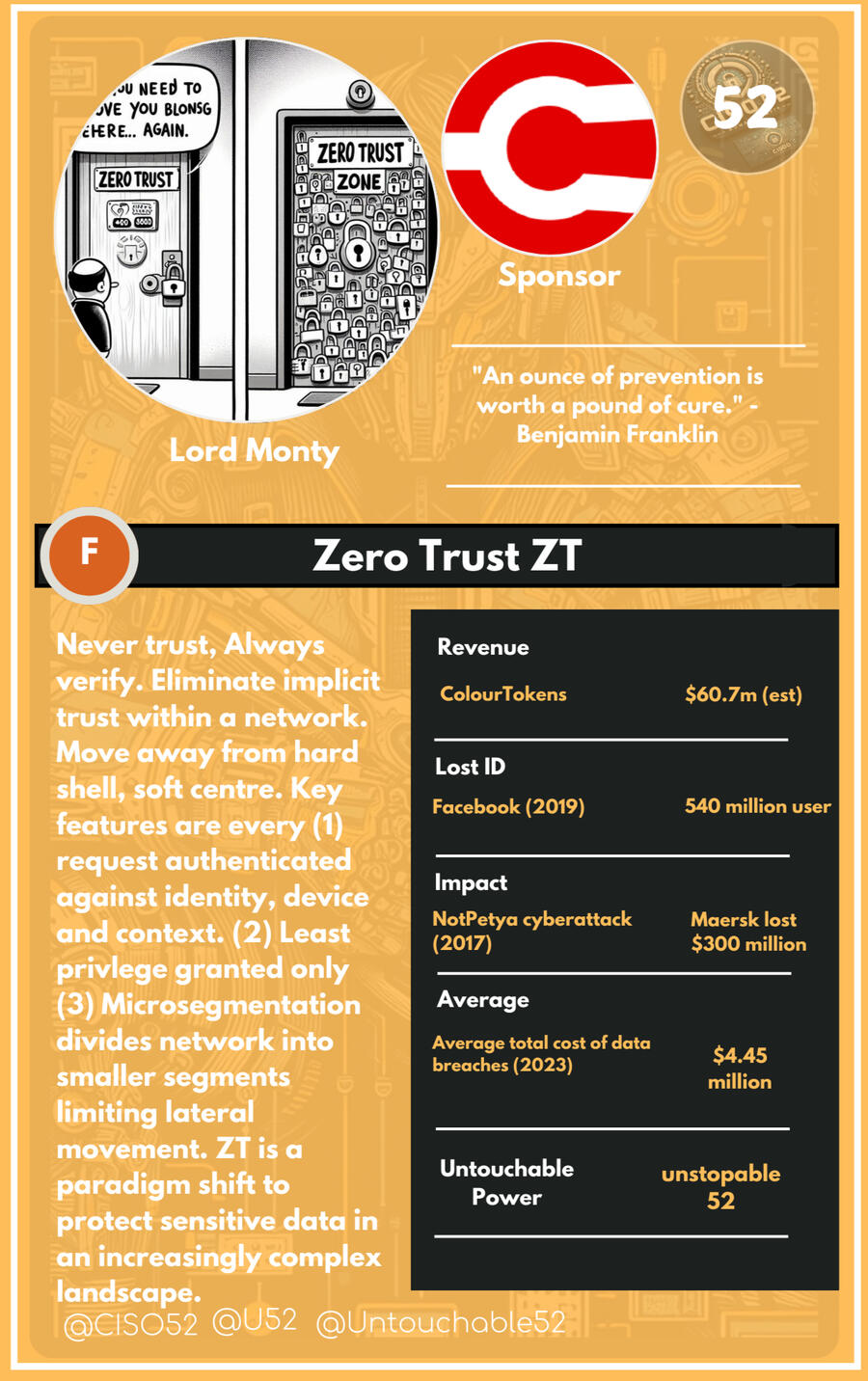
We've developed a unique card game featuring 52 cyber ingredients, with Zero Trust as the untouchable 52nd card. This game serves as an educational tool and a framework for understanding the cybersecurity universe

Why Choose CISO 52?
Our Model
Unique 52-point model addressing the entire cybersecurity landscape
Mastering the Foundations
Focus on the "Triple Threat" for comprehensive protection
Gamification
Innovative gamification approach to cybersecurity.
Our Services
Your Journey
#Bridge #Superstructure #Engine Room #Hull #PassengersThe PASSENGERS(customers) are the focus and beneficiaries of the journey. The SUPERSTRUCTURE (grc) guides the overall direction and ensures compliance. The ENGINE ROOM (operations) powers the organization's daily functions. The HULL (resilience) protects against threats and ensures continuity. The BRIDGE(leadership) oversees and coordinates all these elements.
Strategy bridge
The Bridge team to support and develop your strategy.
digital trust Superstructure
The GRC helm team to support and develop your digital trust.
operations Engine
The operations engine room team to partner and expand your operations.
Resilience hull
The Resilience team to evolve protection against threats.
Cyber Foundations
Ready to build your cyber security plan ?
Get in touch with CISO52 today.